Tombstone scammers steal dead identities mostly for three reasons – to commit financial frauds, enjoy medical benefits or perform criminal acts behind a cloned individual. But the best part of this cyber attack is that the victim will never discover the crime and others will not expect cybercriminals on his/her deathbed. Reetwika cautions and suggests ways to counter such attacks, in the weekly column, exclusively for Different Truths.
Have you ever heard of Tombstone Attack before? This was not so common in India earlier but was very frequent in those countries where the citizens are buried under earth after their demise, with a marble plaque mentioning deceased’s full name, residence, dates of birth and death in remembrance. However, with the increasing population, Tombstone attackers have started flooding our government hospital morgues in search of death records.
Losing our near and dear ones make us so grief-stricken that we often forget to call off their identity proofs like Driving License, PAN card, Aadhar Card, Voter ID, Ration Card, Electricity energy meter, Gas connection, Passport, Bank accounts and passbooks, Debit and Credit cards, Paired loyalty cards, Bank lockers, Investments, Postpaid phone numbers, Internet connections etc to the respective statutory authorities. And our utter bereavement stimulates Tombstone attackers who misuse those dormant  identities to carry out their criminal acts hiding behind the dead.
identities to carry out their criminal acts hiding behind the dead.
Tombstone scammers steal dead identities mostly for three reasons – to commit financial frauds, enjoy medical benefits or perform criminal acts behind a cloned individual. But the best part of this cyber attack is that the victim will never discover the crime and others will not expect cybercriminals at his/her deathbed.
If you see, it is very easy for grave robbers to steal personally indefinable information like name, address, date of birth etc from the plaques as there will hardly be anyone to notice them in the graveyard. By the time it is detected, the attacker would have already committed the crime by spoofing the stolen IDs. There are no reliable ways to trace them back as barely any cemetery in the world will have CCTVs installed.
So, it is very important for us to take timely actions to prevent any cybercrimes targeted at our departed kindreds. Loss of a family person will always be painful but it is also our duty to protect their good names even after passing away. You may like to take the following actions immediately after a bereavement to prevent Tombstone attackers from stealing the cadaver’s identity:
1. Report with a death certificate to the respective regulatory authorities and surrender all the ID proofs immediately after demise. This will prevent any kind of theft of his/her identity.
2. Be alert to unsolicited email or SMS in his personal accounts indicating any use of his financial cards, medical insurance or banking transactions.
3. Request respective social media admin teams to take down his/her public profiles so that catfishers cannot clone their accounts.
4. Be careful of any phishing emails, especially those received at his/her online banking linked accounts.
5. Do not entertain unidentified phone calls on his/her mobile number. Attackers might prank you to disclose all the confidential personal information of the deceased and get a credit card issued in his/her name.
6. Take immediate action on any inherited property related name transfer. Tombstone scammers await delayed responses from the deceased’s family members and dormant bank accounts with substantial cash balance as there is scarcely anyone to monitor the daily transactions.
7. Surrender any active gas, internet, telephone, etc connections by submitting a copy of the death certificate so that in case of any misuse later, he/she cannot be prosecuted.
8. Keep checking the credit record of the person on a regular basis if you wish to wait till the card expiry.
9. Report to his/her employer to discontinue any tax benefits and salary deductions. It will prevent insider Tombstone attackers from exploiting his/her corporate identity.
10. Last but not the least, however painful it is, try to post a public announcement about his/her death on leading newspapers, municipal gazettes, local Police Station, etc., so that all regulatory authorities have a record of his/her death.
It may also happen otherwise. For example, you may receive a financial statement against a person’s name at your address, email ID or phone whom you are no way connected with. That may indicate Tombstone attack targeted at that person, falsely directed to your address with a hope that you will overlook it as other’s mistake. But as a conscious citizen, you must report any such frauds to the respective organisation directly and prevent others from falling prey to the grave robbers.
©Reetwika Banerjee
Photos from the Internet
#CyberCrime #TombStoneAttack #Hacking #DeadPeopleIdentityTheaft #GraveRobbers #Scammers #DifferentTruths

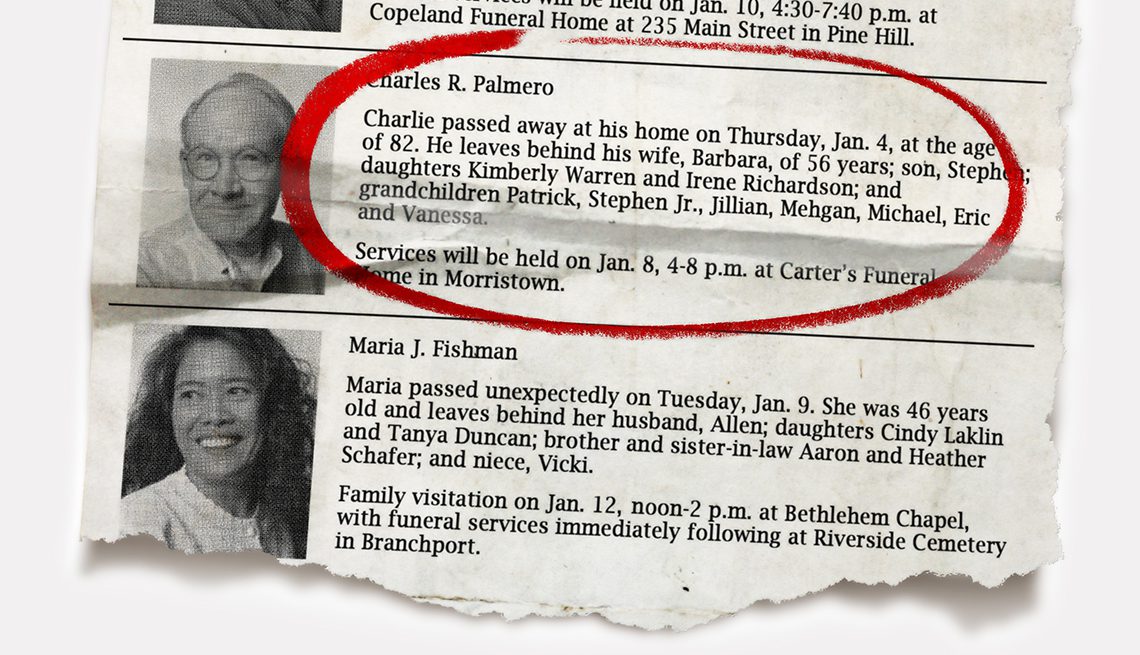





 By
By
 By
By
 By
By