Cyber Security expert, Reetwika, warns us from DroidSheep hijacks on WhatsApp and gives invaluable security tips, in the weekly column. A Different Truths exclusive.
Cyber Security expert, Reetwika, warns us from DroidSheep hijacks on WhatsApp and gives invaluable security tips, in the weekly column. A Different Truths exclusive.
Do you own an Android-based smartphone? Are you a WhatsApp freak?
If your answers to the above questions are both yes, then congratulations! You are highly vulnerable to DroidSheep Attacks. Well, keeping aside technical jargons like all my columns, let me describe what DroidSheep is, its original purpose, how can it be misused and security tips to prevent being hijacked by DroidSheep.
About DroidSheep
DroidSheep is an android based mobile application which was originally developed as a network analysis tool by Andreas Koch for solely security testing purposes and was thus made openly available for free download through the popular online app stores. But with time, thanks to the ill minds, the very operating procedure of the tool proved to be a huge web security threat rather than a technological blessing.
How DroidSheep Operates
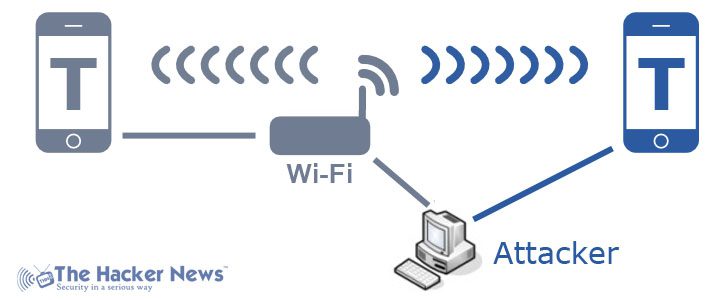
DroidSheep allows any user to capture other’s session IDs over the same wireless network without keeping any trail of its route. In simple words, it can allow intruders to secretly intercept and hijack the web cookies of any authenticated user within the operating range of a wireless network including yours if your device is also connected.
These web cookies are typically the live conversations between sender and receiver, example – your  WhatsApp pings, Messenger chats, Facebook private messages, LinkedIn Inmails, Tweets, Hangout chats, Yahoo IMs etc. Basically, the list includes all mobile chatting applications which you access using an Android-based smartphone.
WhatsApp pings, Messenger chats, Facebook private messages, LinkedIn Inmails, Tweets, Hangout chats, Yahoo IMs etc. Basically, the list includes all mobile chatting applications which you access using an Android-based smartphone.
DroidSheep Abuses
DroidSheep is such a powerful tool that it can easily be exploited to perform session hijacking attempts over a wireless network. Once it is enabled, the tool acts as a network router and sniffs all the available traffic within its perimeter. After a thorough analysis, it displays the list of only authenticated and live session profiles.
With the active IDs in hand, hijackers can now easily target to hijack the ones which have weaker security controls with comparatively higher impact prospects; for example the personal profiles of celebrities, the government official in a critical role, national security representatives, defence administrators, bureaucrats, industrialists, key corporates, eminent doctors etc.
The sender will find his/her session as stalled (typically termed as ‘hang’ situation), breaking the original connection and continue uninterruptedly with the stolen session cookie to converse with the recipient. On the contrary, the receiver will never realize when the sender’s web session got hijacked and thus will continue with their normal conversation in most likely cases.
Security Tips
Before sharing security tips, I strongly believe that it is more important to know the anatomy of an attack so that my readers can identify a cyber attack right at its source and thus can take timely preventive actions, rather proactively, instead of taking corrective steps after the damage is done.
Here you go with my simple tips to prevent DroidSheep hijack attempts:
1. Always use secured wireless connections so that the network data is not openly visible to other connected users. You can check the security protocol of the router or hotspot is possible (WPA and WPA2 are considered as secure Wi-Fi and can be found as displayed on the device body).
2. Do avoid free public Wi-Fi hotspots (ex: airport, hotel, café, metro etc.) for chatting purposes as these are most common epicentres of DroidSheep hijacks.
3. Avoid using your personal smartphone for mission-critical communications; however, time and effort saving it may be. Instead, prefer using secured machines connected to your company’s internal network.
4. In case you have to use a private android based PDA, do install a strong encryption software to secure your private conversations, especially if your messages are critical to national and public security. Even if the session is hijacked, the hackers won’t be able to decode your messages.
5. Install a Virtual Private Network (VPN) at home to connect to official networks so that your network  traffic is protected within an encrypted cloud-based tunnel.
traffic is protected within an encrypted cloud-based tunnel.
6. Verify if your WhatsApp receiver has a security code. It is a good practice to enable dynamic codes than never-changing static ones. Security level will be way higher in the former case because even if the code is compromised once, it will soon get replaced by a system-generated random one.
7. Do not use insecure chatrooms and browsers. You can easily verify this by checking if the messenger has an SSL certificate or not (HTTPS application is SSL certified).
8. Delete all cookies from your device on a regular basis, ideally daily. It can be done from the ‘Settings’ tab of your device.
9. During an ongoing conversation, in an unlikely scenario, if your communication window gets suddenly stalled, keep your chatting partner informed about it preferably via a different media (email, telephone, text message etc.) so that he/she becomes conscious and exits the session immediately. It could be a probable DroidSheep hijack attempt.
10. Last but not the least, this is one of the most common cases. We all have a very bad habit of not exiting our mobile chatrooms. We rather close (or minimise) them, but hardly any of us signs out of the application. Many feel that our device is safe as it is physically with me all the while. But does physical proximity of the smartphone really guaranty your cybersecurity? You should always log out of all private chatrooms once you are finished using them. Remember, this prevents 90% of session hijacking attempts.
©Reetwika Banerjee
Photos from the Internet
#CyberSecurity #CyberCrime #DroidSheep #Chatrooms #Chats #Messenger #Whatsapp #Hacking #DiffrentTruths