A cybersecurity expert, Reetwika tells us about a very fashionable cybercrime which is raving the global payment card industry with a snowballing trend of monetary scams, especially where the card is not present during transactions like e-commerce purchases, online payments etc. As a cardholder, it’s time for us to know how we are exposed to such threats so that we may take timely actions to protect information present on our payment card from falling under wrong hands. She cautions us, in the weekly column, exclusively for Different Truths.
A cybersecurity expert, Reetwika tells us about a very fashionable cybercrime which is raving the global payment card industry with a snowballing trend of monetary scams, especially where the card is not present during transactions like e-commerce purchases, online payments etc. As a cardholder, it’s time for us to know how we are exposed to such threats so that we may take timely actions to protect information present on our payment card from falling under wrong hands. She cautions us, in the weekly column, exclusively for Different Truths.
We live in a payment card era today, surrounded by thousands of debit cards, credit cards, forex cards, prepaid cards, loyalty cards etc. issued by banks, financial organisations, non-bank organisations, travel and entertainment industry, merchandising firms, petroleum, telecommunications and national assignments – each card is uniquely identifiable with the imprinted digits and cardholder data. And where there is data, there is always the risk of data leakage, eventually leading to cyber attacks and financial frauds.
In today’s column, we will look into a very fashionable cybercrime which is raving the global payment card industry with a snowballing trend of monetary scams, especially where the card is not present during transactions like e-commerce purchases, online payments etc. As a cardholder, it’s time for us to know how we are exposed to such threats so that we may take timely actions to protect information present on our payment card from falling under wrong hands.
Well, however protective you may be with the physical card, thanks to cloud computing, the data stored in it can be easily tapped by any cyber mastermind. He does not have to do much but to guess only a few digits of the entire card number because the majority of the digits are programmed and not randomly allotted, which makes the cybercriminal’s task even easier. He only needs to guess the last few digits of your card if he can catch hold of the issuer’s range.
Scientific prediction of a payment card’s correct sequence is known as BIN Attack where BIN stands for Bank (or Issuer) Identification Number. BINs play a very critical role in authenticating any card-based transaction by validating the issuer information with the card used. However, to better appreciate the functional aspect of the attack, let us first spend a few minutes in understanding the anatomy of any standard payment card.
Anatomy of Payment Card
It is important to mention here that cardholder data may refer to any information contained in the respective customer’s payment card. These details are printed on both sides of the card and stored in digital format either on the magnetic strip embedded at the backside of the card or in an electronic chip placed in front.
The anterior side usually contains the following information:
· Card Issuer Brand (ex: Visa, MasterCard, Discover, American Express, JCB etc.)
· Card Type (Classic, Standard, Gold, Platinum, Titanium, etc.)
· Primary Account Number (PAN) which includes BIN
· Cardholder name
· Issue Date
· Expiry Date or Valid Through Date
The magnetic strip at the reverse side or the electronic chip contains these sensitive data required for further authentication and authorization during transactions: –
· Security Code
· CAV2/ CVC2/ CVV/ CVV2/ CID
· PIN/ PIN block
These three are considered as Sensitive Authentication Data (SAD) and no merchants or service providers are permitted to store them for processing purposes. Only the initial cardholder data can be recorded if required.
Analysing Bank Identification Number (BIN)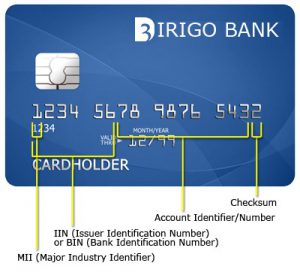
Any payment card comprises of 12 to 16 digits, depending on the card’s brand which is called the cardholder’s Primary Account Number (PAN). The firstdigit is called Major Industry Identifier (MII) and identifies the industry assignment of the card. For example: If the first digit of your payment card is 3, it’s a non-bank card likely to be issued by American Express, Diner’s Club, JCB, etc.; if 4, it means a Visa card; similarly, 5 signifies a MasterCard and so on.
The BIN is a part of the overall Primary Account Number (PAN), usually first 4 to 6 digits, which identifies the payment card brand, issuing bank or authority, type of card along with the sequence of that card lot. If the MII is 9, then the next three digits of BIN signify the 3-digit country code as per ISO 3166 standard.
Unfortunately, there are lots of online BIN verification databases freely available where anyone can validate the authenticity of a given BIN along with the respective card type’s maximum transaction limit.
The next set of 5 to 9 digits signifies the Account Identification Numbers which are unique to each card, however, they too are not absolutely random in the true sense. There does exist some backend logic which could be cracked using advanced computerized permutation-combination based algorithms.
The job becomes easier if the BIN of a card series is already known and verified. As an additional advantage, typically, cards with same BIN have the same expiry dates. Only the account identifiers are unique to each card. Basically, if you observe, out of 12 to 16 digits, only 5 or 9 digits need to be predicted correctly to generate a legitimate card number.
The last digit of the PAN represents a checksum which is required by the issuing bank to verify if a given sequence is a valid card number or not during transaction processing. Thanks to geniuses, now that can also be verified easily using a simple technique – the ‘Luhn Mod-10’ formula. Just follow these simple steps to verify if a given sequence is a valid card number:
Step 1: After you have chalked out a genuine BIN, predict the remaining 5 to 9 digits to create a random sequence resembling a 12 to 16 digit payment card.
Step 2: Double the value of alternate digits beginning with the second digit from the right (the first right-hand digit is the checksum).
Step 3: For any resulting value greater than or equal to 10, subtract 9.
Step 4: Add the calculated values as well as the values skipped in Step 3 together.
Step 5: If the total obtained in Step 4 is a number ending with zero (ex: 30, 40, 50, etc.) then bingo! The sequence you just tried luck is a valid payment card.
Nowadays, collecting BINs is not much of a hassle. The transaction transcripts are already available displaying unmasked BINs (only Account Identification Numbers are hidden), thinking that as a safe practice. Nevertheless, with a set of BINs in hand and a few random Luhn attempts, any computer geek can generate a set of valid cards and commit financial frauds the way he wants. The user will have no clues to detect where it went wrong.
Tips to Prevent Becoming BIN Attack Targets
The above exercise must have helped you to realise how easy it is to guess a payment card information even  though you kept it materially safe in your locker. Thus, physical safety is not the only key to card security. You must take additional measures to prevent becoming BIN Attack targets. Here I share some easy tips which will come handy for developing a safe payment card usage habit: –
though you kept it materially safe in your locker. Thus, physical safety is not the only key to card security. You must take additional measures to prevent becoming BIN Attack targets. Here I share some easy tips which will come handy for developing a safe payment card usage habit: –
1. Never ever share your card’s Sensitive Authentication Data (SAD) like a PIN, CVV, Transaction password etc., with anyone else, even if asked for. They are never required to be shared for processing a transaction. Only the issuing bank and your card’s brand require this piece of information while validating a transaction at the backend which is essentially always an electronic process. Punch in the PINs as and when required, do not save or share with anyone personally.
2. Merchants and card issuing banks have incorporated multiple authentication mechanisms on top of PINs to ensure authorization before processing payments. Extend your cooperation and help them in their endeavours to keep your card information safe.
3. Always keep a close eye on your payment card bills and transaction receipts. Report immediately to your bank and Police in case of any unauthorized transaction (however small it may be), card theft or misplacement. That can be a precursor trailer of a bigger cyberattack. If a cheat gets hold of your legitimate card, he can try to generate valid card numbers based on your BIN and expiry date.
4. Opt for SMS alerts for all your financial transactions so that in case of any unwanted transactions, you are notified instantly.
5. Prefer to use electronic chip-based cards rather than magnetic strips. Chips are more secure than the latter.
6. While making online purchases, always prefer to use your cards only with merchants who have a PCI-DSS certification. It is mandatory for all compliant merchants to display the message on their payment gateway window and thus it is very easy to identify whether a merchant is PCI-DSS compliant or not.
7. Always use an updated Antivirus in your personal device before using your card for any online payment. That’s a basic shield against any potential cybercrime including BIN attack attempts.
8. Never take a photocopy or click a snap of your payment card and share it with external parties. No merchant or service provider should require it as per current payment card industry’s security norms.
9. Do not take help of others while withdrawing cash from ATM, card swipes etc. It is a good practice to swipe the card yourself at POS terminals rather than trusting an unknown person.
10. If you have a budget assigned for cybersecurity, you may also install a licensed version of a fraud detection software to track deceitful use of your payment cards anywhere over the network.
©Reetwika Banerjee
Photos from the Internet
#CyberSecurity #BINAttacks #CyberCrime #MoneySafety #PaymentCards #Network #Fauds #DifferentTruths




 By
By
 By
By
 By
By