Janus was the double-headed Roman God of Gateways, depicting a transitional connection between our past and future. In light of cybercrime, the message sender or originator is pigeonholed as ‘past’ while the recipient is characterised by ‘future’; and the man-in-the-middle or perpetrator is epitomised as ‘Janus’ due to his mythological depiction with two reverse looking identical faces serving as the connecting link between sender and receiver. Reetwika warns us, suggesting ways to safeguard ourselves from such attacks, in the weekly column. A Different Truths exclusive.
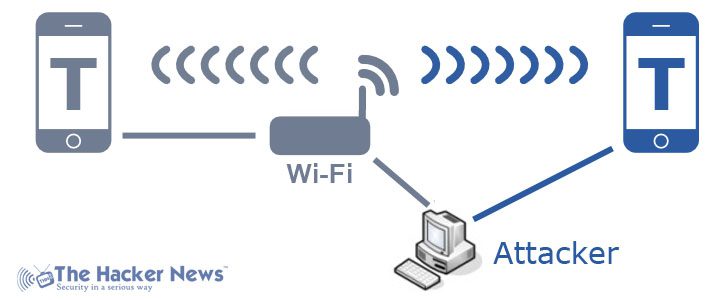
Janus Attack is a pretty trendy name of an age-old kind of cybercrime where during a remote conversation, an intruder impersonates himself as the legitimate receiver to a message sender and vice versa to the receiver, thus unlawfully gaining access to their private communications. Depending upon the level of intrusion, he may also alter the messages shared across the compromised channel or medium.
Now, as a techno buff, an immediate question may arise, why is such a cybercrime termed as Janus Attack? Though there are multiple schools of thought surrounding the naming of this type of attack; here you go with one of the most popular explanations.
Janus was the double-headed Roman God of Gateways, depicting a transitional connection between our past and future. In light of cybercrime, the message sender or originator is pigeonholed as ‘past’ while the recipient is characterised by ‘future’; and the man-in-the-middle or perpetrator is epitomised as ‘Janus’ due to his mythological depiction with two reverse looking identical faces serving as the connecting link between sender and receiver.
Types of Janus Attack
There are primarily five ways by which an attacker may intrude into an ongoing conversation –  Eavesdropping, Session Hijacking, IP Spoofing, Email Phishing and Wi-Fi Rogue Access Point – all of which are different forms of Janus Attack.
Eavesdropping, Session Hijacking, IP Spoofing, Email Phishing and Wi-Fi Rogue Access Point – all of which are different forms of Janus Attack.
Eavesdropping – This is very similar to a postman silently opening a sealed envelope with a secret message, read it, reseal and then handover the envelope to its designated receiver. Neither the sender nor the recipient know about the theft. Now, this postman can misuse the message for any sort of crime, leaving behind absolutely no traces of the manipulation.
Likewise, in a cyber world, any unknown perpetrator can keep a passive watch on your private emails behind anyone’s knowledge.
Session Hijacking – You may imagine it like an extended case of the earlier example. Supposedly, if the postman actively replaces the original message with a false one, none of the sender or receiver will come to know about the substitution right away.
Similarly, during an online cash transfer, after you have authenticated yourself to your bank’s server, a man-in-the-middle can hijack your active session and carry forward the money transfer to his own account. By the time you come to know about it, it’s damn too late.
IP Spoofing – It is a perfect case of impersonation. The attacker can pose to the sender as the legitimate recipient by faking recipient’s IP address or vice versa. Both will accept the intruder believing him as the trusted party and share their personal information over emails, chats etc. But in reality, their messages will never reach each other; only the man-in-the-middle will get to know their authentic bidirectional communications.
Email Phishing – This is one of the easiest ways to deceive people. Taking forward the previous  example, if the postman requests the receiver to collect his envelope from an unknown external location, the receiver agrees to come and then gets abducted by the postman.
example, if the postman requests the receiver to collect his envelope from an unknown external location, the receiver agrees to come and then gets abducted by the postman.
Now, if you extrapolate the instance to a cyber medium, the attacker first tempts a user to click on a fake hyperlink sent via email, taps his or her authentication credentials like username and password, then impersonates to legitimate recipients as the original sender and eventually tricks them to reveal confidential information.
Wi-Fi Rogue Access Point – This is perhaps the most common of all Janus Attack variants. Nowadays, free Wi-Fi hotspots are widely available in airports, cafes, markets, malls, metros, trains, etc., for open public usage. And there are thousands of users who are using it for internet access on the go. But don’t forget, one among those users is a cybercriminal too silently spreading his trap to hunt foolish users who keep checking their personal emails, social media profiles, salary slips, bank accounts, official documents, health records etc., using the free Wi-Fi. Being an insecure connection, such wireless networks never provide the required user protection, thus making the job easier for the attackers. They can sniff, steal, replace, adulterate any communication they want to accomplish their targets.
Security Tips to Prevent Janus Attack
Knowing all this brings us back to the million-dollar question, as a conscious cyber user, how may I protect myself from falling prey to these Janus Attackers? I am sure, my simple tips shared below will surely help to improve your overall security posture.
- As a bare minimum, you must have a strong antivirus with firewall and antispyware protection in place. Try to avoid free solutions to the maximum extent possible as they only provide partial security with their freeware versions.
- Stop accessing insecure websites, especially those without SSL certificates (examples: web chat rooms, unregistered play stores, game zones, unknown video conferencing environments, advertising based travel forums, personal blogs, pornographic sites, gambling centres, betting circles, online casinos, cyber brokers, hacker’s world, deep and dark webs, etc).
Wondering how will you identify any website’ security certificate as a layman? Well, you don’t need to be a cyber geek for that. Just ensure, while you open any website through a browser, the hyperlink must read ‘https’ and not just ‘http’. The ‘s’ along with an adjacent lock symbol signifies SSL certification. Any website with ‘https’ is a trusted one, though there are ways to penetrate ‘https’ traffic as well, but chances are very rare compared to open ‘http’ traffic.
- Do not use public free Wi-Fi hotspots for sensitive transactions and communications. The network owner and intruders can easily read your messages, passwords, keys, etc., entered in clear text. Prefer to use your personal dongle instead.
- Use standard encryption software or hashing algorithms to protect your information from being disclosed to the illegitimate audience. Even if someone succeeds in sniffing your packets, they will not be able to make sense out of it if properly encoded.
But there is a catch here. You must not share the decryption key with your receiver over the same medium. Use other ways like a phone call, voice message, SMS, courier text, etc., to share private keys just how ATM cards and PINs are not provided together.
- Do not open unsolicited phones, SMS, emails, web advertisements, popups, etc., with unknown hyperlinks. Most of the cases they divert you to a phished website to capture your keys, login credentials, passwords, IP address, cookies etc. In India, you may report such suspicious phishing cases to this toll-free number 1800 110 420.
- Modify default username-password combos of all your personal router and network devices. Also, prefer to keep changing them every 45 days as a best practice.
- Do not install non-standard web browsers as private browsers often come with malicious plugins, malware, and other spyware threats.
- Remember to always log out of any secured or insecure authenticated session after use. This must be practiced in mobile apps as well.
- With a flexible budget for security investment, you can think to set up a virtual private network if you frequently need to work from home or use a personal smartphone for official purposes.
- As an additional level of personal security, you may also install a Secure/Multipurpose Internet Mail Extension (S/MIME) along with Digital Signature to ensure non-repudiation of your e-messages, emails or chats.
©Reetwika Banerjee
Photos from the Internet
#CyberCrime #DigitalSignature #SpywareThreats #Cookie #WiFi #Evedropping #IPSpoofing #JanusAttack #DifferentTruths






 By
By
 By
By
 By
By